Why Now
Ransomware aimed at industrial organizations jumped 87% in 2024, with 1,693 victims listed on leak sites—manufacturing still tops the target list and energy/utilities are rising. Boards now expect OT resilience plans with clear KPIs, not just policies. (Dragos)
Executive Summary
- •Threat reality. OT/ICS environments face ransomware that degrades availability and forces manual workarounds; MITRE's ICS matrix explicitly tracks Loss of Availability (T0826) as an adversary goal. (MITRE ATT&CK)
- •Architecture first. Use zones & conduits (IEC 62443) and a DMZ between enterprise IT and control networks; design "blast-radius" limits per process cell. (isa.org)
- •Backups that actually restore. Keep offline/immutable backups and test them; this moved from "best practice" to written federal guidance in 2025. (CISA)
- •Drill what you plan to do. Establish a quarterly tabletop/exercise cadence and track MTTR and coverage % of ransomware playbooks using CISA's ready-made packages. (CISA)
- •Standards mapping. Tie controls to NIST CSF 2.0 functions and NIST SP 800-82r3 for OT, with IEC 62443 for segmentation/security levels. (NIST)
- •Regulatory pressure. NIS2 is now transposed across the EU (Oct 17, 2024), with ENISA's 2024 threat report naming ransomware among top risks: Singapore's OT Masterplan 2024 pushes drills and segmentation at national scale. (Digital Strategy EU)
- •Proof points. 2024–25 incidents at American Water and Schneider Electric illustrate operational disruption risks and the cost of weak segmentation and recovery readiness. (Reuters)
1) Threat & Abuse Cases (Mapped to MITRE ATT&CK/DEFEND)
Ransomware in OT = Availability Attacks
Modern crews favor double-extortion and opportunistic lateral movement from IT into OT-adjacent systems, then encryption of historian/HMI/engineering workstations to halt operations—precisely T0826 Loss of Availability in MITRE ICS ATT&CK. (MITRE ATT&CK)
Initial Access & Pivot
Common paths are remote services, credential reuse, unmanaged jump hosts, and poorly segmented Level 3.5/DMZ tiers—patterns regularly reflected in CISA advisories and cross-sector CPGs. Measure your exposure by counting flat links between enterprise and Level 3/3.5 networks. (CISA)
Sector Data
Dragos' 2025 Year in Review reported 1,693 industrial ransomware cases in 2024 (+87% YoY), with manufacturing most impacted and increased pressure on energy/utilities. Treat these stats as an upper bound of observed activity, not total prevalence. (Dragos)
2) Architecture & Controls (Mapped to Standards)
Anchor to NIST CSF 2.0
Build your program across Identify–Protect–Detect–Respond–Recover and the new Govern function; treat models, historian data, and backup systems as explicit assets with risk owners. (NIST)
OT Design Canon: IEC 62443 Zones & Conduits
- Define zones per process cell; assign Security Levels (SL 1–4) based on consequence and threat.
- Place an industrial DMZ (Level 3.5) to mediate IT/OT data flows; use allow-list rules, unidirectional gateways where feasible, and brokered services (patch proxy, historian replication). (isa.org)
Operational Playbook from NIST SP 800-82r3
Apply OT-specific safeguards (deterministic comms, change control on PLC/RTU configurations, maintenance-window updates) and ensure safety functions are independent from IT identity stores. (NIST Publications)
Backups That Survive Ransomware (CISA 2025)
- Maintain offline, encrypted backups.
- Regularly test availability/integrity.
- Assume actors attempt to locate and encrypt reachable backups. Track Recovery Time Objective (RTO) and Restore Success Rate as KPIs. (CISA)
EU Implementation Guidance for NIS2
ENISA's 2025 technical guide details network segmentation and effectiveness assessments—use it to justify funding for segmentation and exercise metrics. (ENISA)
3) Case Studies (What They Teach)
American Water (Oct 2024)
The largest U.S. water utility disconnected systems, paused billing, and worked through recovery after a cyber incident; operations were reportedly not impacted, but business systems were. Lesson: business-OT interdependencies matter—protect customer/billing platforms to prevent cascading operational risk. (Reuters)
Schneider Electric (Nov 2024)
A breach of internal platforms and earlier disruption to a business unit highlighted supplier and platform risk even for security-mature vendors. Lesson: require incident-notification SLAs and attestations from key OT vendors. (The Wall Street Journal)
Industrial Ransomware Trend (2024→2025)
Dragos tracked Q4 2024 and Q2 2025 incident volumes; the narrative shows persistent pressure on industrials despite quarter-to-quarter fluctuation. Lesson: make resilience a program, not a project. (Dragos)
4) Economics (FAIR-Style): Where to Spend First
| Scenario (per site, per year) | Est. Frequency λ | P90 Loss (USD) | Control Change | ΔAttack Surface | Notes |
|---|---|---|---|---|---|
| Lateral movement from IT to Level 3 | 3.0 | 600k | Create 3.5 DMZ + strict conduits | −50% | Cuts flat links; small perf hit |
| Historian/HMI encryption | 1.0 | 1.8M | Immutable offline backups + restore drills | −35% | RTO ↓; production halts shorter |
| Engineering workstation compromise | 0.7 | 2.5M | App-allowlisting + signed images | −30% | Aligns w/ 800-82r3 |
| Supplier remote access abuse | 0.5 | 1.2M | Privileged access broker + JIT | −40% | Contracted KPI + audit trails |
| Patch/backup infra targeted | 0.6 | 900k | Separate admin forest + vault | −45% | Common blind spot |
Price controls by ΔExpected Loss, not vendor feature lists; show boards MTTR, backup restore success, and conduit coverage %.
5) Governance: Policy, Audits, Cadence, Supplier Risk
- Policy set. An OT Cybersecurity Standard referencing NIST CSF 2.0, SP 800-82r3, and IEC 62443; define security levels by zone and require conduit allow-lists documented in change records. (NIST)
- Audit trails. Immutable logs for remote access, engineering changes, and backup restores; align with NIS2 oversight and incident-reporting expectations. (Digital Strategy EU)
- Red-team & exercises. Run quarterly ransomware tabletops/functional drills using CISA CTEPs; publish MTTR and drill coverage to leadership. (CISA)
- Supplier controls. Require SBOM/VEX and secure-by-design attestations; tie to contracts with notification SLAs (DORA/NIS2 adjacencies for entities with EU footprint). (Digital Strategy EU)
6) Implementation Playbook (30/60/90 Days, with KPIs)
Days 0–30 (Stabilize)
- Inventory zones/conduits; count flat IT↔OT links; set target of −40% links by Day 90.
- Enforce backup hygiene: one offline copy; schedule restore tests for top 3 HMIs/historians. KPI: Restore Success ≥95%. (CISA)
- Stand up access broker for vendor remote access; require MFA + session recording.
Days 31–60 (Segmentation & Drills)
- Build/validate Level 3.5 DMZ; implement allow-listed data flows (historians, patch proxy). KPI: Conduit Policy Coverage ≥80%. (isa.org)
- Run a CISA tabletop focused on ransomware in OT; record MTTR from detection → isolation → restore. KPI: MTTR ≤ 8h to safe state. (CISA)
Days 61–90 (Prove Recovery)
- Perform unannounced restore drill of a historian snapshot; validate RTO versus production tolerance.
- Contractually bind supplier notification and remote access controls, test revocation.
- Executive review: present ΔAttack Surface, MTTR trend, and backup test pass-rate mapped to CSF 2.0. (NIST)
7) Regulatory Landscape (US/EU + Singapore)
- United States. CISA Stop Ransomware Guide (2025 update) codifies offline/immutable backups and routine testing; use CPGs to justify baseline investments and board metrics. (CISA)
- European Union. NIS2 national laws effective Oct 17–18, 2024 increase oversight and incident-handling obligations; ENISA Threat Landscape 2024 ranks ransomware among prime threats; new ENISA 2025 implementation guidance details segmentation and effectiveness testing. (Digital Strategy EU)
- Singapore (third market). OT Cybersecurity Masterplan 2024 renews focus on segmentation, exercises, and sector uplift—use as a reference model for APAC plants. (Cyber Security Agency of Singapore)
8) What to Watch Next (12 Months)
- Industrial leak-site telemetry. Track Dragos quarterly ransomware posts to validate trend direction in your sector and region. (Dragos)
- NIS2 enforcement clarity. Watch national regulators' audit expectations for segmentation proofs and exercise evidence. (Digital Strategy EU)
- CISA exercise ecosystem. Expanding CTEP content and CPG assessment tooling will make KPI-driven resilience easier for mid-market operators. (CISA)
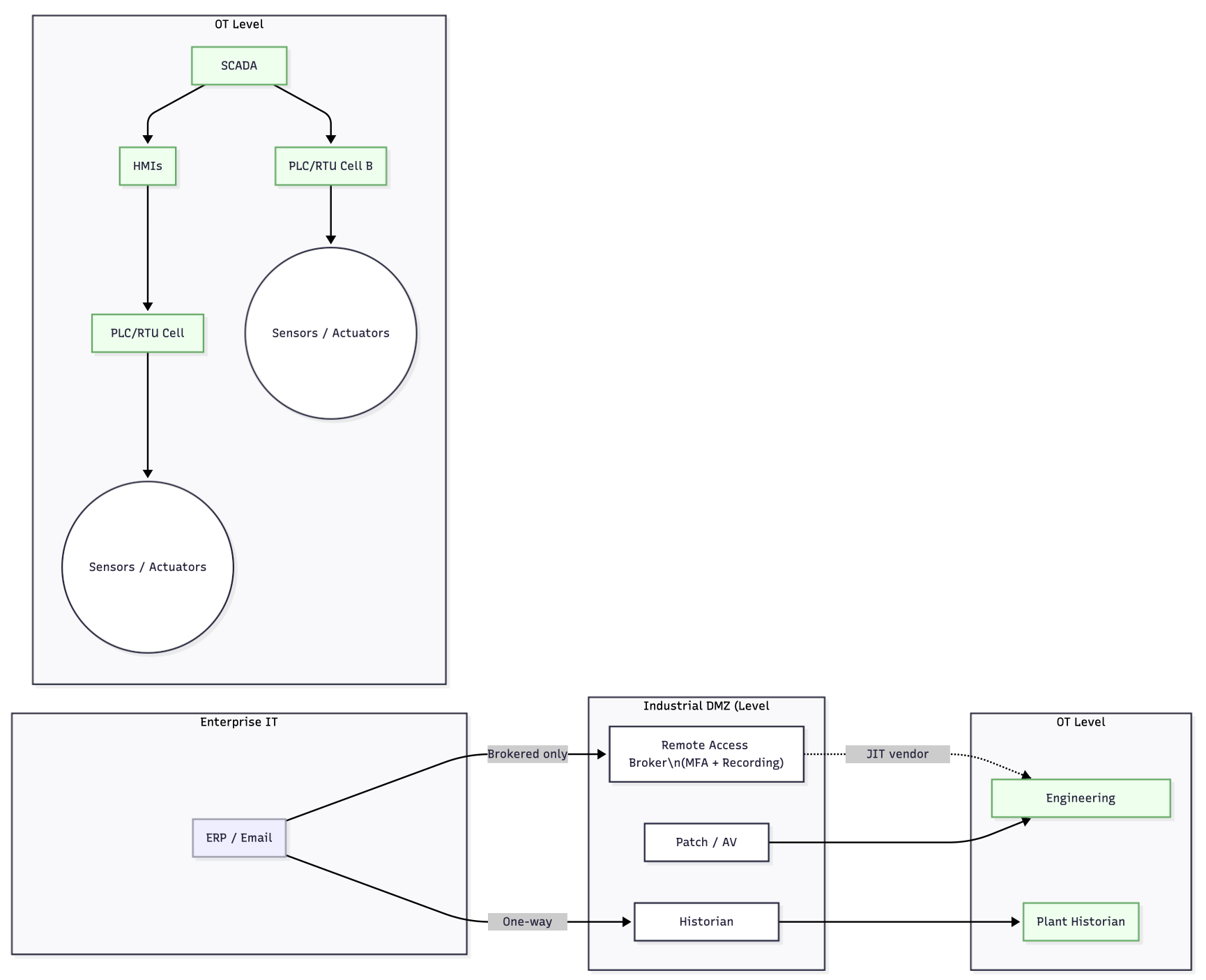
Figure 1 — Segmented OT network for ransomware resilience
Figure 2 — Guarding accuracy vs latency & cost
Fact-Check Table
| Claim | Source | Date | Confidence (1–5) |
|---|---|---|---|
| Industrial ransomware cases: 1,693 in 2024 (+87% YoY) | Dragos YIR 2025 | Feb 25 2025 | 4 |
| MITRE ICS technique T0826 Loss of Availability applies | MITRE ATT&CK for ICS | Accessed 2025 | 5 |
| Offline, encrypted backups and regular testing recommended | CISA Stop Ransomware (2025 PDF) | Mar 2025 | 5 |
| NIS2 transposition deadline Oct 17, 2024 | EU Digital Strategy | Oct–Nov 2024 | 5 |
| ENISA lists ransomware among prime 2024 threats | ENISA Threat Landscape 2024 | Sep–Oct 2024 | 5 |
| American Water incident paused billing; operations not impacted | Reuters/AP | Oct 2024 | 4 |
| Schneider Electric cyber incident disclosed Nov 2024 | WSJ | Nov 2024 | 4 |
Sources
- NIST. Cybersecurity Framework (CSF) 2.0 (Feb 26, 2024). (NIST)
- NIST. SP 800-82r3: Guide to Operational Technology (OT) Security (Sept 28, 2023). (NIST Publications)
- ISA/IEC. 62443 Series (zones & conduits overview) (accessed 2025). (isa.org)
- CISA. Stop Ransomware Guide (updated 2025)—offline, encrypted backups and regular restore testing. (CISA)
- CISA. Tabletop Exercise Packages (CTEP) (2025). (CISA)
- ENISA. Threat Landscape 2024 (Sept–Oct 2024). (ENISA)
- ENISA. Technical Implementation Guidance for NIS2 measures (June 2025) — segmentation & effectiveness testing. (ENISA)
- Dragos. 8th Annual OT Cybersecurity Year in Review (2025)—1,693 industrial ransomware cases in 2024 (+87% YoY). (Dragos)
- MITRE. ATT&CK for ICS (T0826 Loss of Availability). (MITRE ATT&CK)
- EU Commission. NIS2 transposition deadline (Oct 17, 2024). (Digital Strategy EU)
- Case references: American Water (Oct 2024); Schneider Electric (Nov 2024). (Reuters)
